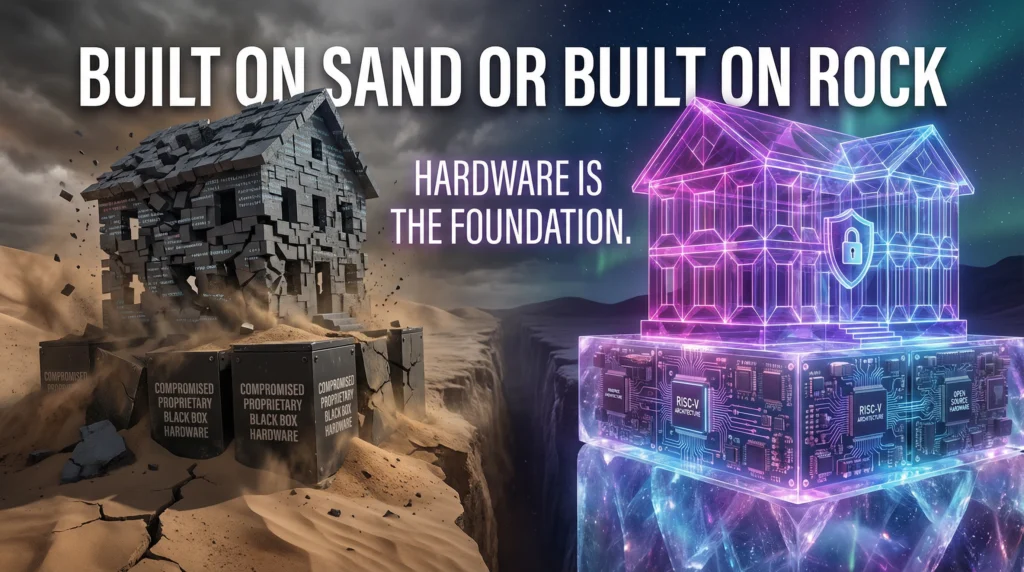
The Sovereignty Series (Part 4 of 5): Building on Bedrock, Not Sand
So far in our journey toward digital sovereignty, we have established a powerful new philosophy. We began by accepting that all systems will be compromised, forcing us to adopt a Zero Trust model of constant, cryptographic verification. We then made this model resilient by embracing Decentralization, creating a system with no single point of failure. We have designed a beautiful, secure house. But we have ignored the most important question of all: what is it built on?
All the sophisticated cryptography, decentralized consensus, and zero-knowledge proofs in the world are utterly meaningless if the hardware they run on is compromised. If the silicon itself is lying to you, then the entire structure is built on sand. For Europe to be truly sovereign, it cannot just control its software and its networks; it must be able to trust the physical chips that form the foundation of its digital world.
The Black Box Problem
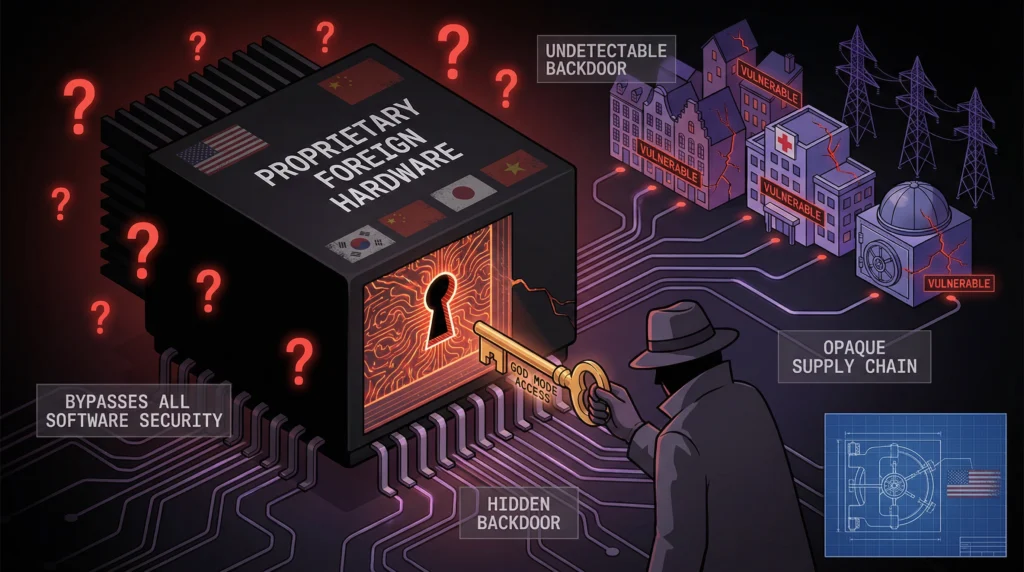
Today, Europe’s digital infrastructure runs almost entirely on hardware designed and manufactured elsewhere, primarily in the United States and Asia. These chips are, for all intents and purposes, black boxes. Their internal designs are proprietary trade secrets, and their complex global supply chains are opaque and impossible to fully audit. This creates a terrifying and unacceptable vulnerability.
A malicious backdoor could be etched directly into the silicon during the manufacturing process. This kind of hardware-level compromise is the holy grail for an intelligence agency. It is persistent, it is virtually undetectable by any software, and it can be used to bypass all other security measures. It gives the manufacturer—and by extension, their government—a permanent “god mode” access to the system. Relying on foreign, black-box hardware for our critical infrastructure is the digital equivalent of building a national bank and letting a rival nation design the vault.
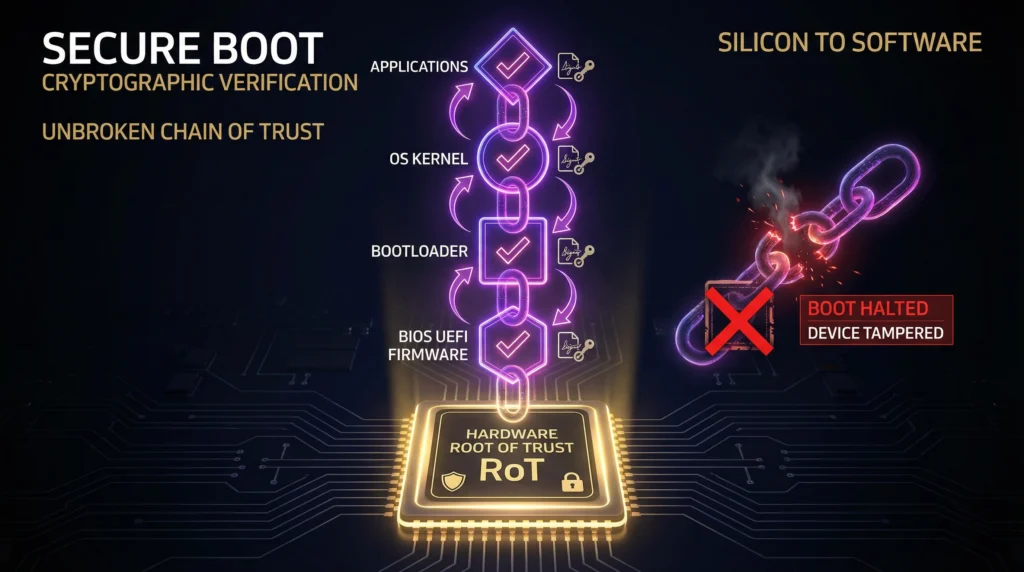
The Hardware Root of Trust
To solve this, we must establish trust at the lowest possible level. We need a Hardware Root of Trust (RoT)—a component that is inherently trustworthy and can serve as the anchor for the security of the entire system. A RoT is a secure, isolated environment within a processor that can perform cryptographic functions and attest to the state of the device. It is the first link in a secure chain.
When a device with a RoT powers on, it doesn’t just blindly start loading software. It begins a process called Secure Boot. The RoT first verifies the cryptographic signature of the initial firmware (the BIOS/UEFI). If and only if that signature is valid, the firmware is allowed to run. The firmware then verifies the signature of the operating system bootloader, which in turn verifies the OS kernel, and so on. This creates an unbroken, verifiable chain of trust from the silicon to the software. If any component in that chain has been tampered with, the boot process halts, and the system refuses to start.
The Only Solutions: Open-Source Hardware
But how can we trust the Root of Trust itself? If the RoT chip is another black box from a foreign supplier, we have only moved the problem down one level. The only way to truly trust the hardware is to be able to see exactly how it is designed. The only path to a verifiable Hardware Root of Trust is through open-source hardware.
This is where initiatives like RISC-V become critically important. RISC-V is an open-source instruction set architecture (ISA)—the fundamental language that a computer processor speaks. Because it is open, anyone can inspect it, use it, and build upon it. It removes the proprietary lock-in that has defined the semiconductor industry for decades.
Building on this, projects like OpenTitan are creating open-source designs for the silicon Root of Trust chips themselves. This means that for the first time, we can have a fully transparent, auditable security foundation for our computers. We can inspect the blueprints of the vault before we build it.
For Europe, this is not an academic exercise. It is a strategic imperative. Achieving digital sovereignty requires a massive investment in and a public procurement mandate for open-source hardware. We must foster a European semiconductor industry that is not just building chips, but building trustworthy chips based on transparent, open designs.
This is the bedrock. A verifiable, open-source hardware foundation is the only thing upon which a truly secure and sovereign digital infrastructure can be built. With this final piece in place, we are ready to assemble the full picture. In our concluding post, we will lay out the complete, step-by-step roadmap for Europe to achieve genuine digital independence.
Previous:
The Sovereignty Series (Part 2 of 5): Never Trust, Always Verify
Next:
The Sovereignty Series (Part 5 of 5): The Blueprint for Independence
Do It all on Our Own Hardware:
#HardwareRootOfTrust #OpenSourceHardware #RISCV #OpenTitan #SecureBoot #HardwareSecurity #DigitalSovereignty #SemiconductorSecurity #TrustworthyHardware #SupplyChainSecurity #HardwareBackdoors #CryptographicVerification #SecureEnclave #TrustedComputing #HardwareTransparency