ISO 27001 Based on IT Baseline Protection – The Royal Road for Public Authorities
Meta Description: ISO 27001 certification based on IT Baseline Protection (IT-Grundschutz). The proven path for the public sector. BSI-compliant, secure, and efficient.
Why IT Baseline Protection is the Standard for Public Authorities
The BSI’s IT Baseline Protection is more than a recommendation; it is the de facto standard for information security in German public administration. It offers concrete measures, field-tested building blocks, and a clear methodology, which makes it incredibly valuable.
An ISO 27001 certification is internationally recognized and demonstrates a functioning Information Security Management System (ISMS). Combining these two worlds is ideal: the specific guidelines of IT Baseline Protection fulfill the abstract requirements of ISO 27001.
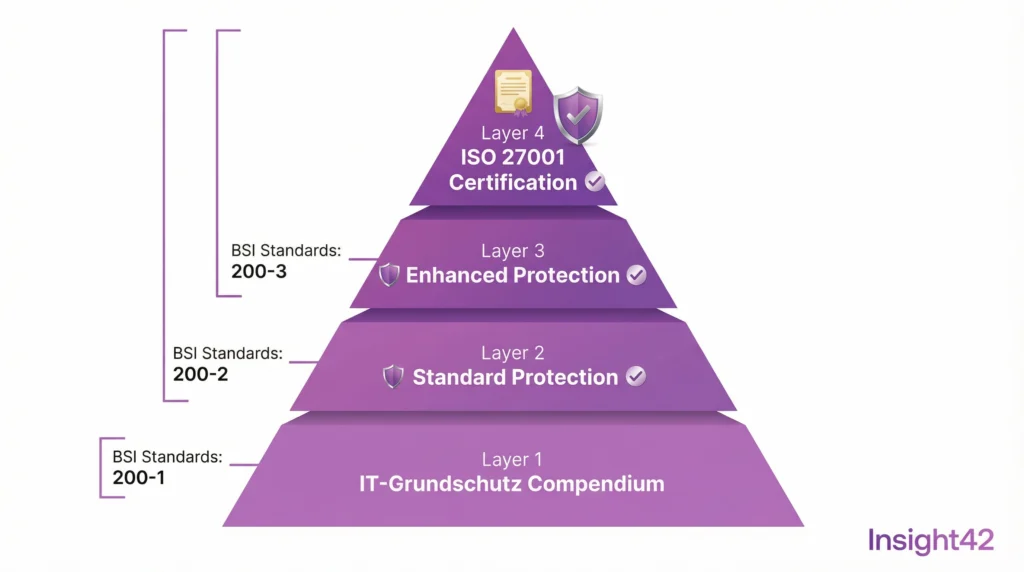
The Synergy of IT Baseline Protection and ISO 27001
ISO 27001 requires an ISMS but does not specify how to implement it. IT Baseline Protection provides exactly that: a detailed guide. Those who implement IT Baseline Protection have already done most of the work for an ISO 27001 certification.
The advantages of this combination:
- Concrete and Field-Tested: IT Baseline Protection offers ready-made building blocks.
- BSI-Recognized: The methodology is well-established within the German public sector.
- Efficient: It avoids duplication of effort.
- Internationally Recognized: The ISO 27001 certification builds trust.
The Path to Certification
Step 1: Structural Analysis
Which information, processes, and IT systems need protection? The structural analysis defines the scope of the ISMS.
Step 2: Protection Needs Assessment
How critical is the data? Normal, high, or very high? The protection needs assessment evaluates the requirements for confidentiality, integrity, and availability.
Step 3: Modeling According to IT Baseline Protection
The identified systems are mapped to the building blocks of the IT-Grundschutz Compendium. The result is a list of relevant requirements.
Step 4: Basic Security Check
This is a gap analysis. Which requirements are already implemented? Where are the gaps? The basic security check identifies the need for action.
Step 5: Implementation and Audit
The gaps are closed. The ISMS is put into practice. An external auditor verifies conformity and issues the ISO 27001 certificate.
Quick Checklist: ISO 27001 Based on IT Baseline Protection
| Phase | Task | Status |
| 1. Preparation | Define Scope | ☐ |
| 2. Analysis | Conduct Structural Analysis | ☐ |
| 3. Assessment | Determine Protection Needs | ☐ |
| 4. Modeling | Map IT Baseline Protection Building Blocks | ☐ |
| 5. Gap Analysis | Perform Basic Security Check | ☐ |
| 6. Implementation | Execute Action Plan | ☐ |
| 7. Audit | Certification Audit | ☐ |
To-Do List for Project Managers
- Immediately: Secure management commitment.
- Week 1: Appoint an ISMS team.
- Week 2: Commission IT Baseline Protection consulting.
- Month 1: Start the structural analysis.
- Month 2: Complete the protection needs assessment.
- Quarter 2: Conduct the basic security check.
- Quarters 3-4: Implement measures.
- Next Year: Plan the certification audit.
IT Baseline Protection in the Cloud
The principles of IT Baseline Protection also apply in the cloud, but the implementation differs. Responsibility is shared. Cloud providers (Azure, GCP) deliver a secure foundation, while the authority is responsible for secure configuration and use (Shared Responsibility Model).
An ISO 27001 certification based on IT Baseline Protection for cloud workloads is possible. It requires a clear understanding of responsibilities. BSI C5 Cloud requirements are also integrated here. The BSI-compliant cloud security concept documents the implementation.
Insight42: Your Partner for IT Baseline Protection
We are experts in ISO 27001 based on IT Baseline Protection. We understand the requirements of the public sector. Our IT Baseline Protection consulting is field-tested and efficient.
We guide you from the initial analysis to successful certification and beyond, with managed services for continuous security and compliance.
Start on the secure path. Contact us.
Figure: The Synergy of IT Baseline Protection and ISO 27001
Blog Post 2: IT Baseline Protection in the Cloud – Practical Implementation in Azure and GCP
Meta Description: Practically implement IT Baseline Protection in the cloud. ISO 27001 based on IT-Grundschutz for Azure and GCP. BSI C5 compliant, secure, and for public authorities.
IT Baseline Protection Meets the Cloud
IT Baseline Protection is not limited to on-premises environments. Its principles are universal, but implementation in the cloud requires a new way of thinking. The Shared Responsibility Model is key. Who is responsible for what? This question must be answered clearly.
For the public sector, cloud migration means reinterpreting IT Baseline Protection. The building blocks do not change, but the way the requirements are met does. Automation and cloud-native tools play a central role.
The Shared Responsibility Model in Detail
- Cloud Provider (e.g., Azure, GCP): Responsible for the security of the cloud. This includes the physical security of data centers, the security of the virtualization layer, and the basic infrastructure.
- Customer (Authority): Responsible for security in the cloud. This includes service configuration, identity and access management, data protection, and operating system patching.
IT Baseline Protection consulting helps to define this demarcation clearly. The BSI-compliant cloud security concept documents it.
Implementing Baseline Protection Building Blocks in the Cloud
OPS.1.1.5: Logging
- Azure: Azure Monitor, Log Analytics, Microsoft Sentinel
- GCP: Cloud Logging, Cloud Monitoring, Chronicle SIEM
- Implementation: Enable logging for all services. Define retention periods. Automate analysis.
CON.1: Cryptography
- Azure: Azure Key Vault, Always Encrypted, Transparent Data Encryption
- GCP: Cloud Key Management Service, Confidential Computing
- Implementation: Enforce data-in-transit and data-at-rest encryption. Centralize key management.
ORP.4: Identity and Access Management
- Azure: Entra ID, Conditional Access, Privileged Identity Management (PIM)
- GCP: Cloud Identity, Identity-Aware Proxy (IAP), IAM Conditions
- Implementation: Apply Zero Trust principles. Enforce MFA. Implement least privilege.
NET.1.1: Network Architecture
- Azure: Virtual Network, Network Security Groups, Azure Firewall
- GCP: Virtual Private Cloud (VPC), Firewall Rules, Cloud Armor
- Implementation: Use hub-and-spoke or VPC peering. Enforce network segmentation. Activate DDoS protection.
Quick Checklist: IT Baseline Protection in the Cloud
| Baseline Protection Building Block | Cloud Tool (Azure Example) | Implemented? |
| ORP.4 (IAM) | Entra ID, PIM | ☐ |
| CON.1 (Crypto) | Key Vault, TDE | ☐ |
| OPS.1.1.5 (Logging) | Log Analytics, Sentinel | ☐ |
| NET.1.1 (Network) | VNet, NSGs, Firewall | ☐ |
| SYS.1.1 (Server) | Azure Policy, Defender for Cloud | ☐ |
| DER.1 (Secure Development) | Azure DevOps Security | ☐ |
To-Do List for Cloud Baseline Protection
- Week 1: Understand and document the Shared Responsibility Model.
- Week 2: Conduct a cloud-specific risk analysis.
- Month 1: Create a mapping of Baseline Protection building blocks to cloud services.
- Month 2: Build a landing zone with Baseline Protection configurations (Policy-as-Code).
- Month 3: Centralize logging and monitoring.
- Ongoing: Monitor compliance status with cloud tools (e.g., Defender for Cloud).
The Role of BSI C5
BSI C5 and IT Baseline Protection are complementary. BSI C5 is a requirements catalog specifically for cloud services. Many C5 requirements can be met directly with Baseline Protection measures. Anyone implementing IT Baseline Protection in the cloud is well on their way to BSI C5 compliance.
The BSI-compliant cloud security concept should integrate both frameworks. It demonstrates how the requirements of C5 and Baseline Protection are met through technical and organizational measures in the cloud.
Insight42: Your Partner for Cloud Security
We translate IT Baseline Protection for the cloud. We show you how to operate Azure and GCP securely and compliantly. Our IT Baseline Protection consulting is specialized for cloud scenarios.
We build secure landing zones that incorporate ISO 27001 and BSI C5 requirements from the start. With Cloud Managed Services, we ensure ongoing secure operations.
Make your cloud Baseline Protection-compliant. Talk to us.
Figure: Implementing IT Baseline Protection Principles in a Cloud Architecture
#ITBaselineProtection #ISO27001 #CloudSecurity #BSIC5 #PublicSector #GovTech #InfoSec #ISMS #Azure #GCP #CloudMigration #Compliance #Cybersecurity #SecurityConcept #CloudFirst #ManagedServices #Insight42 #DigitalTransformation