A Guide for Public Authorities
Meta Description: BSI C5 Cloud certification for the public sector. Audit readiness, compliance requirements, and the BSI-compliant cloud security concept.
What is BSI C5?
BSI C5 is the German standard for cloud security, developed by the Federal Office for Information Security (BSI). It defines minimum requirements for cloud services and is often mandatory for the public sector.
Is cloud migration for the public sector possible without BSI C5? It’s risky. Tenders for cloud migration usually demand it, and the procurement process for cloud service providers verifies the certification.
The Structure of BSI C5
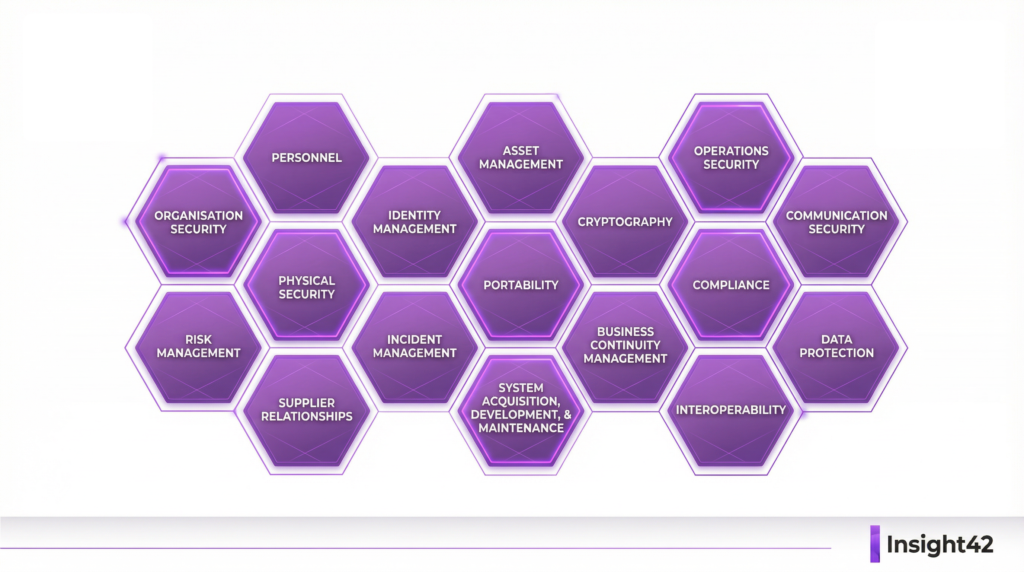
BSI C5 comprises 17 requirement domains, from organization to incident management. Each domain contains specific controls that must be demonstrated.
The 17 Domains at a Glance:
Information Security Organization, Security Policies, Human Resources, Asset Management, Physical Security, Operations Security, Identity and Access Management, Cryptography, Communication Security, Portability and Interoperability, Procurement and Development, Supplier Relationships, Security Incident Management, Compliance, Data Protection, Product Security, Interoperability.
Type 1 vs. Type 2 Attestation
BSI C5 has two attestation types, and the difference is important.
Type 1 Attestation
This assesses the appropriateness of the controls at a specific point in time. Are the controls designed? Are they implemented?
Type 2 Attestation
This assesses the effectiveness of the controls over a period of at least six months. Do the controls work? Are they being followed?
For public authorities, a Type 2 attestation is usually required. It offers more security and demonstrates continuous compliance.
Quick Checklist: BSI C5 Readiness
| Domain | Checkpoint | Status |
| Organization | ISMS Established | ☐ |
| Policies | Security Policies Documented | ☐ |
| Personnel | Awareness Training Conducted | ☐ |
| Assets | Inventory Complete | ☐ |
| Access | IAM Implemented | ☐ |
| Cryptography | Encryption Active | ☐ |
| Logging | Logging Enabled | ☐ |
| Incident | Process Defined | ☐ |
To-Do List for BSI C5 Certification
- Month 1: Conduct a gap analysis.
- Month 2: Create an action plan.
- Months 3-6: Implement controls.
- Month 7: Perform an internal audit.
- Month 8: Conduct an external pre-audit.
- Months 9-10: Undergo the Type 1 audit.
- Months 11-16: Operational phase.
- Month 17: Undergo the Type 2 audit.
The Path to Attestation
Becoming BSI C5 compliant is a project. It requires planning, resources, and expertise.
Step 1: Gap Analysis
Where do you stand today? Which controls are missing? IT baseline protection consulting helps with the assessment. The gap analysis shows the way forward.
Step 2: Action Planning
What measures are necessary? In what order? With what budget? The action plan is created.
Step 3: Implementation
Controls are introduced. Processes are established. Documentation is created. The BSI-compliant cloud security concept is developed.
Step 4: Audit
An auditor conducts the review. The controls are tested. Evidence is collected. The attestation is issued.
Cloud Providers and BSI C5
Major cloud providers like Azure, GCP, and AWS have BSI C5 attestations. But that is not enough. Your use of their services must also be compliant.
Azure migration and GCP migration must consider BSI C5. An Azure Landing Zone and a GCP Landing Zone should incorporate BSI C5 controls. The Cloud Adoption Framework for Azure helps with this.
Insight42 BSI C5 Services
We guide public authorities to BSI C5 compliance, from gap analysis to the audit. We provide the BSI-compliant cloud security concept from a single source.
We offer cloud consulting for authorities with a BSI C5 focus and cloud managed services for continuous compliance. We are an experienced IT service provider for the public sector.
Become BSI C5 compliant. Contact us.
Figure: The Path to BSI C5 Certification
Blog Post 2: Preparing for a BSI C5 Audit – Practical Tips for the Public Sector
Meta Description: BSI C5 audit preparation for public authorities. Practical tips, documentation, and evidence collection. Create a BSI-compliant cloud security concept.
The Audit is Approaching
You have decided on BSI C5. Implementation is underway. Now comes the audit. How do you prepare? What can you expect?
BSI C5 audits are thorough. Auditors want to see evidence, not just documents, but also established practices. This article prepares you.
Documentation is Everything
No attestation without documentation. Auditors can only audit what is documented. Every control needs evidence. Every process needs a description.
What must be documented:
Security policies and their approval, process descriptions with responsibilities, configuration standards and their implementation, employee training records, and logs as proof.
The Most Common Audit Findings
Preparation also means avoiding mistakes. These findings are common:
Incomplete Documentation
Controls exist but are not documented, or the documentation is outdated. Solution: Keep documentation current.
Missing Evidence
Processes are followed but not logged. Solution: Enable logging and recording.
Inconsistent Implementation
Policies exist but are not followed. Solution: Conduct regular internal audits.
Unclear Responsibilities
No one feels responsible. Solution: Create a RACI matrix.
Quick Checklist: Audit Preparation
| Document | Content | Current? |
| ISMS Manual | Overall Security Overview | ☐ |
| Security Policies | All Policies | ☐ |
| Risk Analysis | Current Assessment | ☐ |
| Asset Register | Complete Inventory | ☐ |
| Access Matrix | Permissions Documented | ☐ |
| Incident Log | Incidents Logged | ☐ |
| Training Records | All Employees | ☐ |
| Audit Trail | Changes Traceable | ☐ |
To-Do List for Audit Readiness
- 8 weeks prior: Fully review documentation.
- 6 weeks prior: Conduct an internal pre-audit.
- 4 weeks prior: Remediate findings.
- 2 weeks prior: Compile evidence.
- 1 week prior: Brief interview partners.
- Audit Day: Stay calm, cooperate.
- After Audit: Remediate findings promptly.
The BSI-Compliant Cloud Security Concept
The security concept is the centerpiece. It comprehensively describes your cloud security. Auditors will read it carefully.
Contents of the Security Concept:
Scope and demarcation of cloud use, risk analysis and assessment, technical and organizational measures, responsibilities and processes, and emergency and business continuity management.
IT baseline protection consulting helps with its creation. ISO 27001 based on IT-Grundschutz provides the structure. The result: an audit-proof document.
Mastering Interviews
Auditors conduct interviews. They want to understand how controls are put into practice. Preparation is important.
Tips for Interviews:
Answer honestly. Do not speculate. Ask for clarification if unsure. Have evidence ready. Stay calm.
Employees should know their responsibilities and be able to explain processes. Briefings before the audit help.
Continuous Compliance
BSI C5 is not a one-time project; it is a continuous process. After the audit is before the audit.
Cloud managed services for authorities help with this through continuous monitoring, regular reviews, and automated compliance checks.
Azure managed services and GCP operations provide support with dashboards showing compliance status and alerts for deviations.
Insight42 Audit Support
We guide you through the audit: preparation, execution, and follow-up, with experienced consultants by your side.
We create the BSI-compliant cloud security concept together. IT baseline protection consulting is our core business. BSI C5 compliance is our goal.
Pass your audit. Talk to us.
Figure: BSI C5 Audit Preparation Overview
#BSIC5 #CloudSecurity #Audit #Compliance #PublicSector #GovTech #SecurityConcept #ITBaselineProtection #CloudMigration #Certification #InfoSec #ISMS #CloudFirst #AzureMigration #GCPMigration #ManagedServices #DigitalTransformation #Cybersecurity #Insight42 #Germany
Insight42 – Cloud Migration & Security Consulting
www.insight42.de