
The Sovereignty Series (Part 3 of 5): A System With No Single Point Of Failure
In this series, we first accepted the harsh reality that all digital systems will be breached. Then, we embraced a new security philosophy—Zero Trust—where we assume breach and verify everything, all the time. But even a perfect Zero Trust system can have a fatal flaw if it has a centralized core. If a system has a single brain, a single heart, or a single control panel, it has a single point of failure. And a single point of failure is a single point of control for an adversary.
To build a truly sovereign digital Europe, we must do more than just change our security philosophy. We must fundamentally change the architecture of our digital world. We must move from centralized systems to decentralized ones. We must build a system with no head to cut off.
The Centralization Trap

For the past thirty years, the internet has evolved towards centralization. Our data, our identities, and our digital lives are concentrated in the hands of a few massive corporations and government agencies. We have built a digital world that mirrors the structure of a medieval kingdom: a central castle (the data center) protected by high walls (the firewalls), where a single king (the system administrator) holds absolute power.
As we discussed in the first post, this model is a security nightmare. It creates a single, irresistible target for our adversaries. But the danger is even more profound. A centralized system is not just vulnerable to attack; it is vulnerable to control. A government can compel a company to hand over user data. A malicious insider can alter records. A single bug in the central system can bring the entire network to its knees. This is not sovereignty. It is dependence on a fragile, powerful, and ultimately untrustworthy core.
The Power of the Swarm: What is Decentralization?
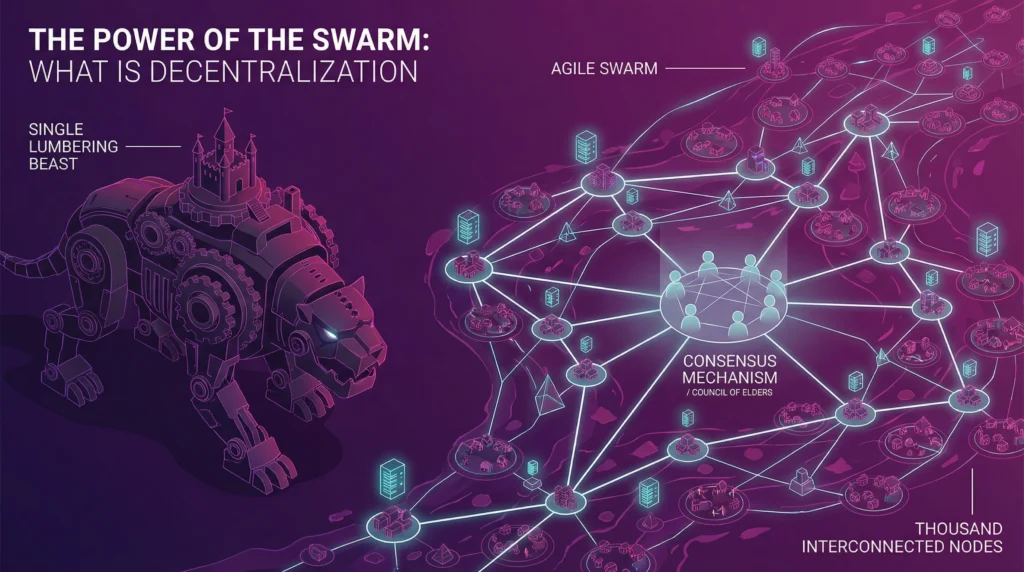
Decentralization means breaking up this central point of control and distributing it across a network of peers. Instead of a single castle, imagine a thousand interconnected villages. Instead of a single king, imagine a council of elders who must reach a consensus. This is the difference between a single, lumbering beast and a resilient, adaptable swarm.
In a decentralized system, there is no single entity in charge. Data is not stored in one place; it is replicated and synchronized across many different nodes in the network. Decisions are not made by a single administrator; they are made through a consensus mechanism, where a majority of participants must agree on the state of the system. This architecture has profound implications for security and sovereignty.
Resilience by Design
A decentralized system is inherently resilient — since it does not have a centrally point of “all control“.
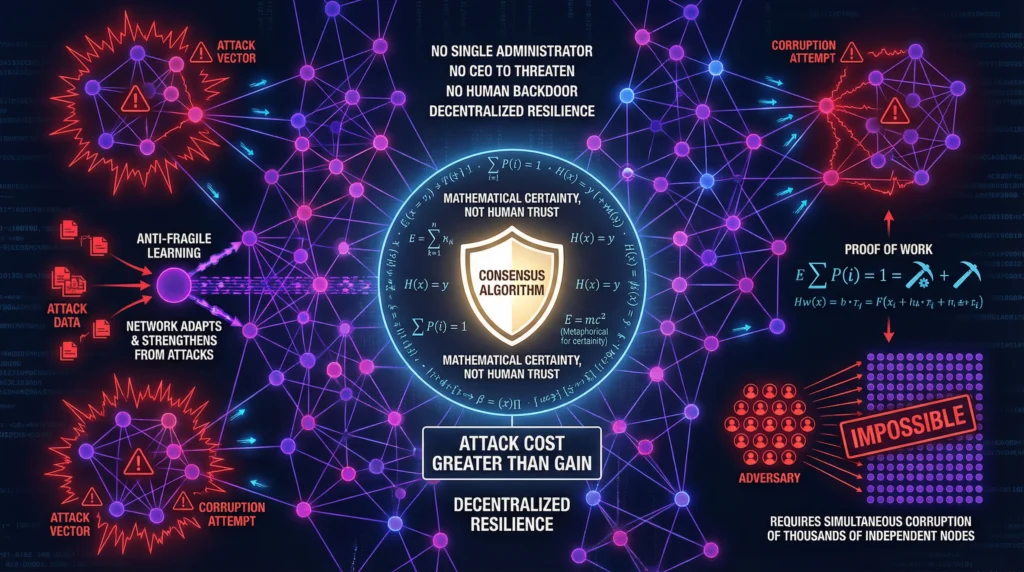
First, it has no single point of failure. If a dozen nodes in the network are attacked, flooded, or simply go offline, the network as a whole continues to function seamlessly. The system is anti-fragile; it can withstand and even learn from attacks on its individual components.
Second, it presents a terrible target for an adversary. Why would a state-level attacker spend millions of euros to compromise a single node in a network of thousands, when doing so grants them no control over the system and their malicious changes would be instantly rejected by the rest of the network? Decentralization diffuses the threat by making a successful attack economically and logistically infeasible.
Finally, it is resistant to corruption and coercion. In a decentralized system, there is no single administrator to bribe, no CEO to threaten, and no politician to pressure. To manipulate the system, you would need to corrupt a majority of the thousands of independent participants simultaneously—a near-impossible task. Trust is not placed in a person or an institution; it is placed in the mathematical certainty of the consensus algorithm.
The Unbreakable Record
This is made possible by the invention of distributed ledger technology (DLT), most famously represented by blockchain. A distributed ledger is a shared, immutable record of transactions that is maintained by a network of computers, not a central authority. Every transaction is cryptographically signed and linked to the previous one, creating a chain of verifiable truth that, once written, cannot be altered without being detected.
This technology allows us to have a shared source of truth without having to trust a central intermediary. It is the architectural backbone of a system where trust is distributed, and power is decentralized.
In our journey towards digital sovereignty, decentralization is not just a technical preference; it is a political necessity. It is the only way to build a digital infrastructure that is truly resilient, censorship-resistant, and free from the control of any single entity, whether it be a foreign power, a tech giant, or even our own government.
But a decentralized software layer is only as secure as the foundation it is built on. In our next post, we will travel to the very bottom of the stack and explore why true sovereignty must begin with the silicon itself: Hardware Security.