
The Sovereignty Series (Part 2 of 5): Never Trust, Always Verify
In our last post, we made a stark declaration: all digital systems will eventually be compromised. The traditional “fortress” model of security is broken because it fails to account for the inevitability of human error, corruption, and deception. If we cannot keep attackers out, how can we possibly build a secure and sovereign digital Europe?
The answer lies in a radical new philosophy, one that is perfectly suited for a world of constant threat. It’s called Zero Trust, and its central mantra is as simple as it is powerful: Never trust, always verify – and it has been proven over decades now.
What is Zero Trust?
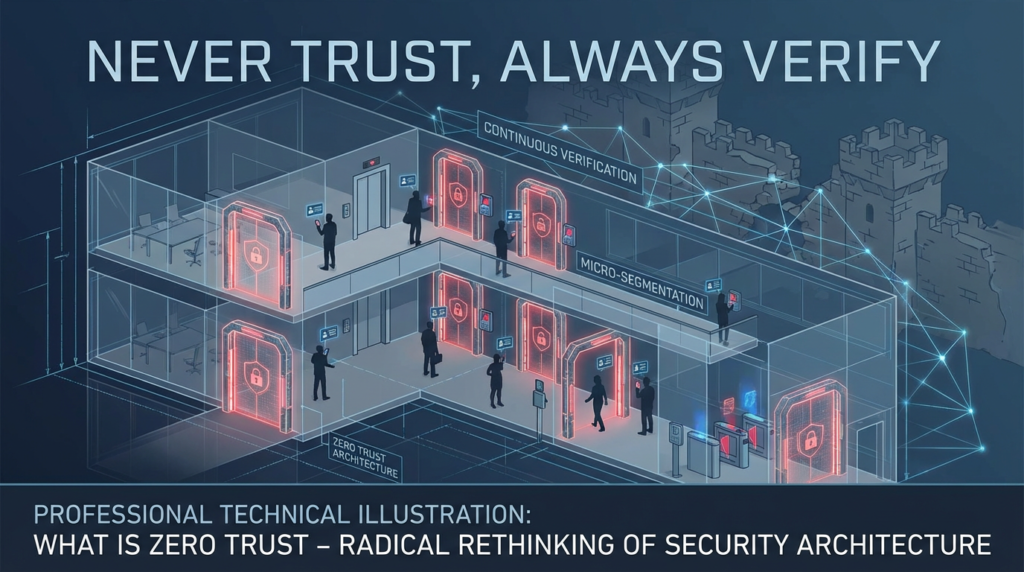
Zero Trust is not a product or a piece of software; it is a complete rethinking of how we approach security. It begins with a single, foundational assumption: the network is already hostile. There is no “inside” and “outside.” There is no “trusted zone.” Every user, every device, and every connection is treated as a potential threat until proven otherwise.
Imagine a world where your office building didn’t have a front door with a single security guard. Instead, to enter any room—even the break room—you had to prove your identity and your authorization to be there, every single time. That is the essence of Zero Trust. It eliminates the very idea of a trusted internal network. An attacker who steals a password or breaches the firewall doesn’t get a free pass to roam the system; they are still an untrusted entity who must prove their right to access every single file or application, one request at a time.
This continuous, relentless verification is the heart of the Zero Trust model. Trust is not a one-time event; it is a dynamic state that must be constantly re-earned. This makes the system incredibly resilient. A compromised device or a stolen credential has a very limited blast radius, because it does not grant the attacker automatic access to anything else.
The Magic of Zero Knowledge: Proving Without Revealing

But Zero Trust on its own is not enough. If every verification requires you to present your sensitive personal data—your driver’s license, your passport, your date of birth—then we have simply moved the problem. We have replaced a single, high-value central database with thousands of smaller, but still sensitive, data transactions. This is where a revolutionary cryptographic technique comes into play: Zero-Knowledge Proofs (ZKPs).
ZKPs are a form of cryptographic magic. They allow you to prove that you know or possess a piece of information without revealing the information itself.
Think about it like this: you want to prove to a bouncer that you are over 21. In the old world, you would show them your driver’s license, which reveals not just your age, but your name, address, and a host of other personal details. In a world with ZKPs, you could simply provide a cryptographic proof that verifiably confirms the statement “I am over 21” is true, without revealing your actual date of birth or any other information. The bouncer learns only the single fact they need to know, and nothing more.
This is a game-changer for privacy and security. It allows us to build systems where verification is constant, but the exposure of personal data is minimal. We can prove our identity, our qualifications, and our authorizations without handing over the raw data to a hundred different services. It is the ultimate expression of “data minimization,” a core principle of Europe’s own GDPR.
The Foundation of True Sovereignty
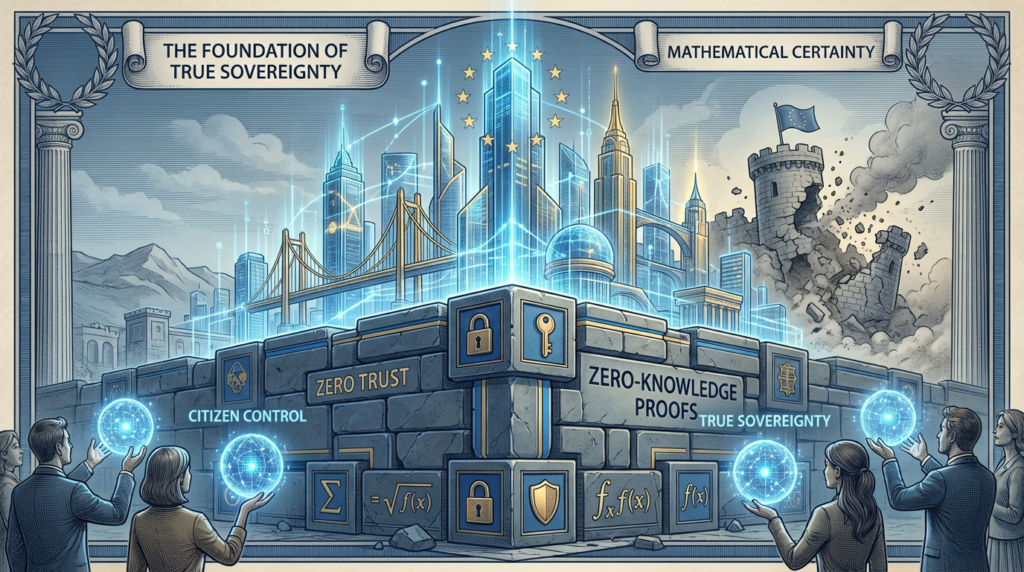
Together, Zero Trust and Zero-Knowledge Proofs form the bedrock of a truly sovereign digital infrastructure. They create a system that is secure not because it is impenetrable, but because it is inherently resilient. It is a system that does not rely on the flawed assumption of human trustworthiness, but on the mathematical certainty of cryptography.
By building on these principles, Europe can create a digital ecosystem that is both secure and respectful of privacy. It can build a system where citizens control their own data and where trust is not a commodity to be bought or sold, but a verifiable fact.
But this is only part of the story. A Zero Trust architecture cannot exist in a vacuum. It must be built on a foundation that is equally resilient. In our next post, we will explore the critical role of Decentralization in building a system with no single point of failure.
#ZeroTrustArchitecture #NeverTrustAlwaysVerify #NeverTrust #AlwaysVerify #ZeroTrustSecurity #ZeroKnowledgeProofs #ContinuousVerification #DigitalSovereignty #CryptographicVerification #DataMinimization #PrivacyPreserving #ZeroTrustImplementation #ResilientSecurity #TrustedNetwork #ContinuousAuthentication #ZeroTrustFramework #IdentityVerification
Previous:
The Sovereignty Series (Part 1 of 5): The Myth of the Impenetrable Fortress
Next:
The Sovereignty Series (Part 3 of 5): A System With No Single Point of Failure