
The introduction of The Sovereignty Series part 1 delves into the concept of cybersecurity long viewed as a fortress. For decades, we’ve been told a simple story about cybersecurity: it’s like building a fortress. To stay safe, we must build higher walls, deeper moats, and stronger gates than our adversaries. We invest in firewalls, intrusion detection systems, and complex passwords—all in an effort to keep the bad guys out. This model, known as perimeter security, has dominated our thinking for a generation. And for a generation, it has been failing. In The Sovereignty Series part 1, we begin to question these outdated models.
In the quest for true digital sovereignty, for an independent Europe that controls its own digital destiny, our first and most critical step is to abandon this flawed metaphor. We must accept a fundamental, uncomfortable truth. All systems will be compromised. As explained in The Sovereignty Series part 1, it is not a matter of if, but when.
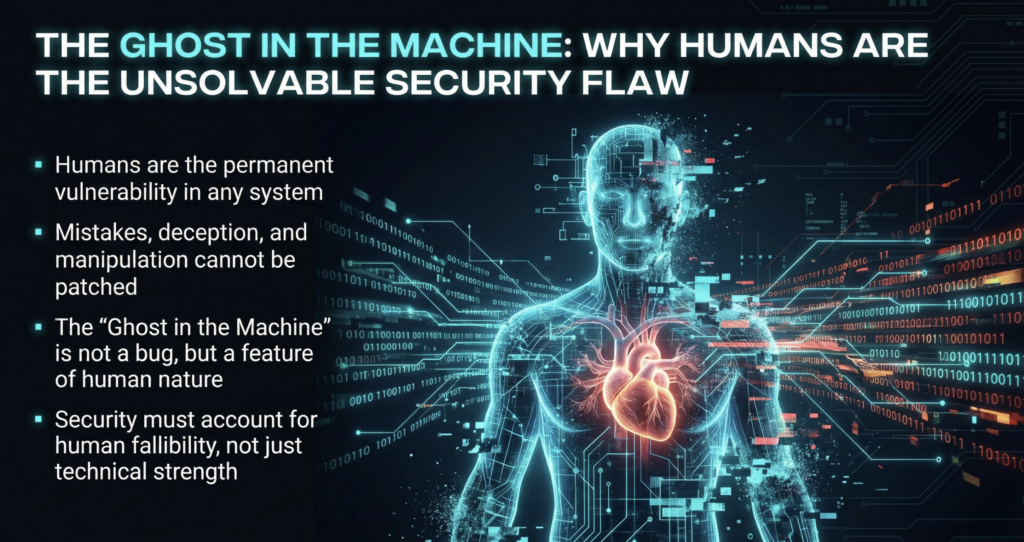
The Human Element: The Ghost in the Machine
The greatest vulnerability in any digital fortress is not in the code or the cryptography; it is in the people who build, maintain, and use it. The human element is a permanent, unsolvable security flaw. Why?
First, humans make mistakes. A simple misconfiguration, a bug in a line of code, or a forgotten security patch—these are the unlocked backdoors through which attackers waltz. The Sovereignty Series part 1 highlights how, in a complex system, the number of potential mistakes is nearly infinite.
Second, humans are susceptible to love and fear. In a centralized system, a handful of administrators hold the keys to the kingdom. These individuals become high-value targets for bribery, extortion, or blackmail. The Families of those even more so! A foreign power doesn’t need to crack a complex algorithm. They can simply buy the password from a worried parent getting a call from his wife. This makes the entire system fragile, resting on the assumption of unwavering human integrity. An assumption that history has repeatedly proven false. He who ever holds the key to the caste, will be a prime target for forces unbound by moral.
Finally, humans are vulnerable to deception. Phishing attacks, which trick users into revealing their credentials, remain one of the most effective infiltration methods. This is because they target human psychology, not technical defenses. No firewall can patch human curiosity or fear. The Series part 1 on sovereignty intensively highlights this aspect.
Finally, a little nudge, a little help here or there, might have a very big effect. Once the state would have central control and a real intractability for low transaction sums, the contradictions in a central system are absolute. A lot of untraceable little transactions will make a theft untraceable.
A central point of being able to trace everything will make the system worse. Since you only have to corrupt one person. Just by knowing who has what where, you can always visit them in the night. And have him gladly pay for the life of his loved ones — a little bit of special motivation granted. But those individuals are good and ruthless in ways of making you happily pay, as explained in The Sovereignty Series part 1.
The Centralization Problem: All Our Eggs in One Broken Basket
Our current digital infrastructure is overwhelmingly centralized. Our data, our identities, and our communications are stored in massive, centralized databases. These are controlled by a few large corporations or government agencies. This architectural choice creates two critical vulnerabilities.
First, it creates a single point of failure. When all your critical data is in one place, that place becomes a target of immense value. The Sovereignty Series part 1 also discusses that a successful breach at the center means a complete, catastrophic failure for the entire system. The attacker doesn’t need to defeat a thousand different defenses. They only need to find one way into the one place that matters.
Second, it makes these systems an irresistible target. For state-sponsored hackers, criminal organizations, and industrial spies, a centralized database of citizen information, financial records, or intellectual property is the ultimate prize. The potential reward is so great that it justifies an almost unlimited investment in time and resources to breach it.
A New Philosophy: Assume Breach
If the fortress model is broken, if the human element is an unsolvable vulnerability, and if centralization creates irresistible targets, then we must conclude that the goal of preventing a breach is futile. In The Series focused on sovereignty, part 1 reveals that the most sophisticated defenses will eventually be bypassed. The most loyal administrator can be compromised. The most secure perimeter will, one day, be crossed.
This realization is not a cause for despair, but for a radical shift in thinking. If we cannot stop attackers from getting in, we must design systems that are secure even when they are compromised. We must build a world where an attacker who has breached the perimeter finds they have gained nothing of value and can do no harm. Stay tuned for further insights in The Sovereignty Series part 1, where this topic is further explored.
This is the foundational principle of a truly sovereign digital future. It requires us to throw out the old blueprints and start fresh. In our next post, we will explore the revolutionary security philosophy that makes this possible: Zero Trust.